These are the configuration changes to be made in the identity provider instance when setting up an OAuth Connection.
These instructions apply to ServiceNow. Other identity providers may vary.
In native ServiceNow, navigate to System OAuth > Application Registry and click New.
On the interceptor page, click Create an OAuth API endpoint for external clients.
The fields to be configured for the Application Registry record are as follows:
Name
Name of the OAuth app
<Your Unique Name>
Client ID*
The client id of the OAuth app
[read-only] (automatically generated)
Client Secret*
The client secret of the OAuth app
Leave [Blank] to automatically generate
Refresh Token Lifespan*
The number of seconds a refresh token issued will be good for
8,640,000 (default value - automatically populated)
Access Token Lifespan*
The number of seconds an access token issued will be good for
1,800 (default value - automatically populated)
Comments
Comments about the OAuth app
<Your description of the purpose of the OAuth entity>
*These values are to be left as-is.
Your Application Registries New Record should look like this:
Submit the record.
If you re-open the record after submitting it, you will see that the Client Secret has been populated.
If you haven't already done so, you will need to create an Inbound user in this instance. See here for details.
In Unifi Integration Designer, navigate to Connections and click New.
We have chosen to configure a Connection for the Pre-Production environment because we have already configured connections in the Consumer Instance for both the Development and Test environments. Choose whichever environment is appropriate for your requirements.
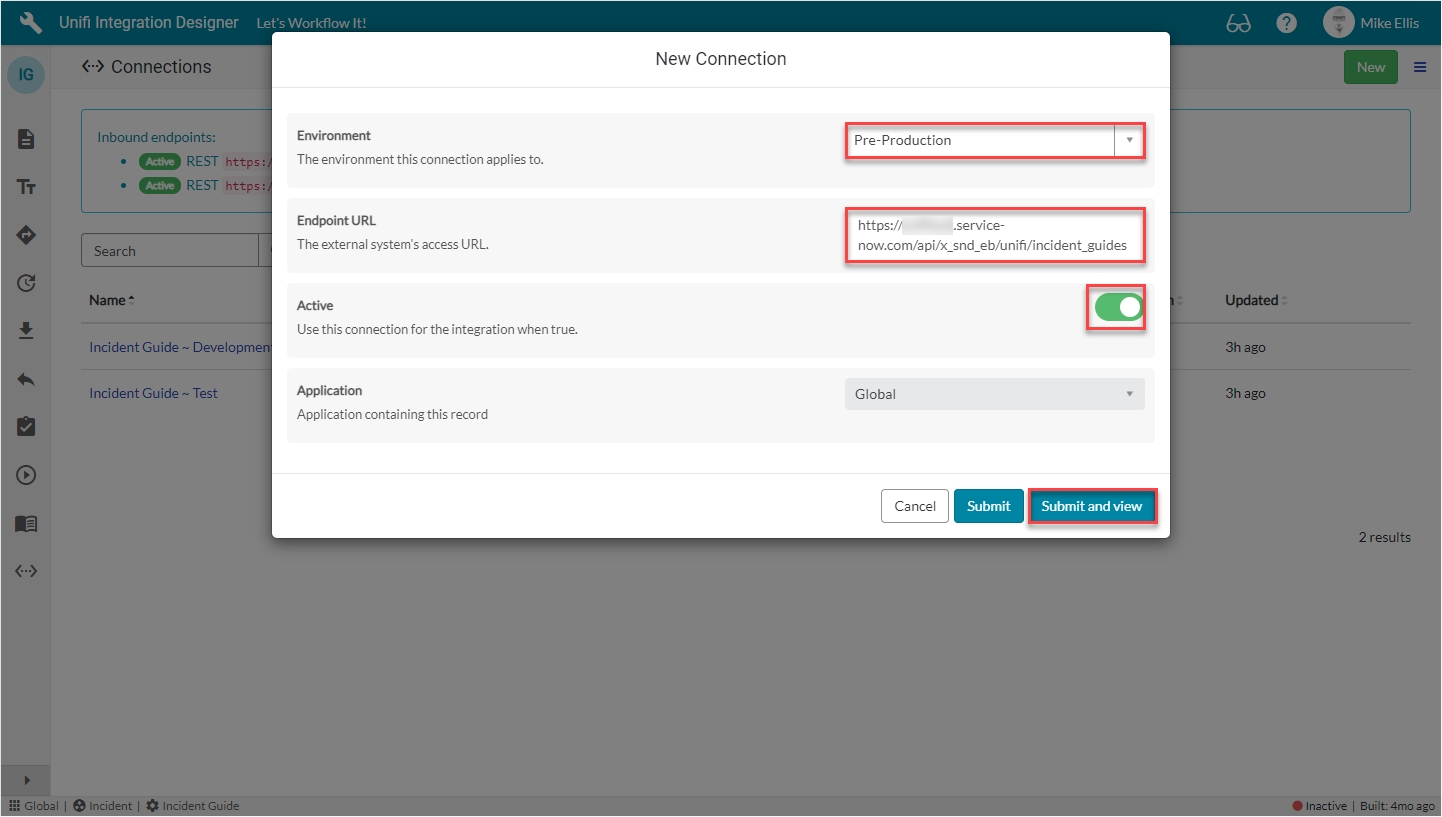
The fields to be configured for the New Connection modal are as follows:
Environment
The environment this connection applies to.
'Pre-Production'
Endpoint URL
The external system's access URL.
<External system Endpoint URL>
Active
Use this connection for the integration when true.
<true>
The format of the Endpoint URL is as follows:
https://<your_consumer_instance>.service-now.com/<your_consumer_resource_path>
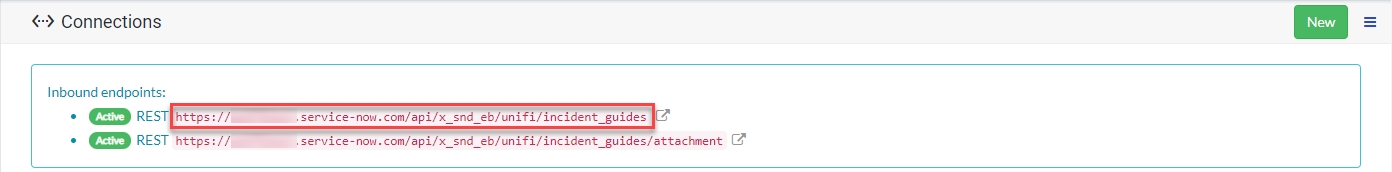
The entire Endpoint URL can be easily obtained from the automatically created Message Resource on the Unifi Scripted REST API (displayed in the widget at the top of the Connections page) in the other instance.
Your New Connection modal should look like this:
Submit and view to further configure the Connection.
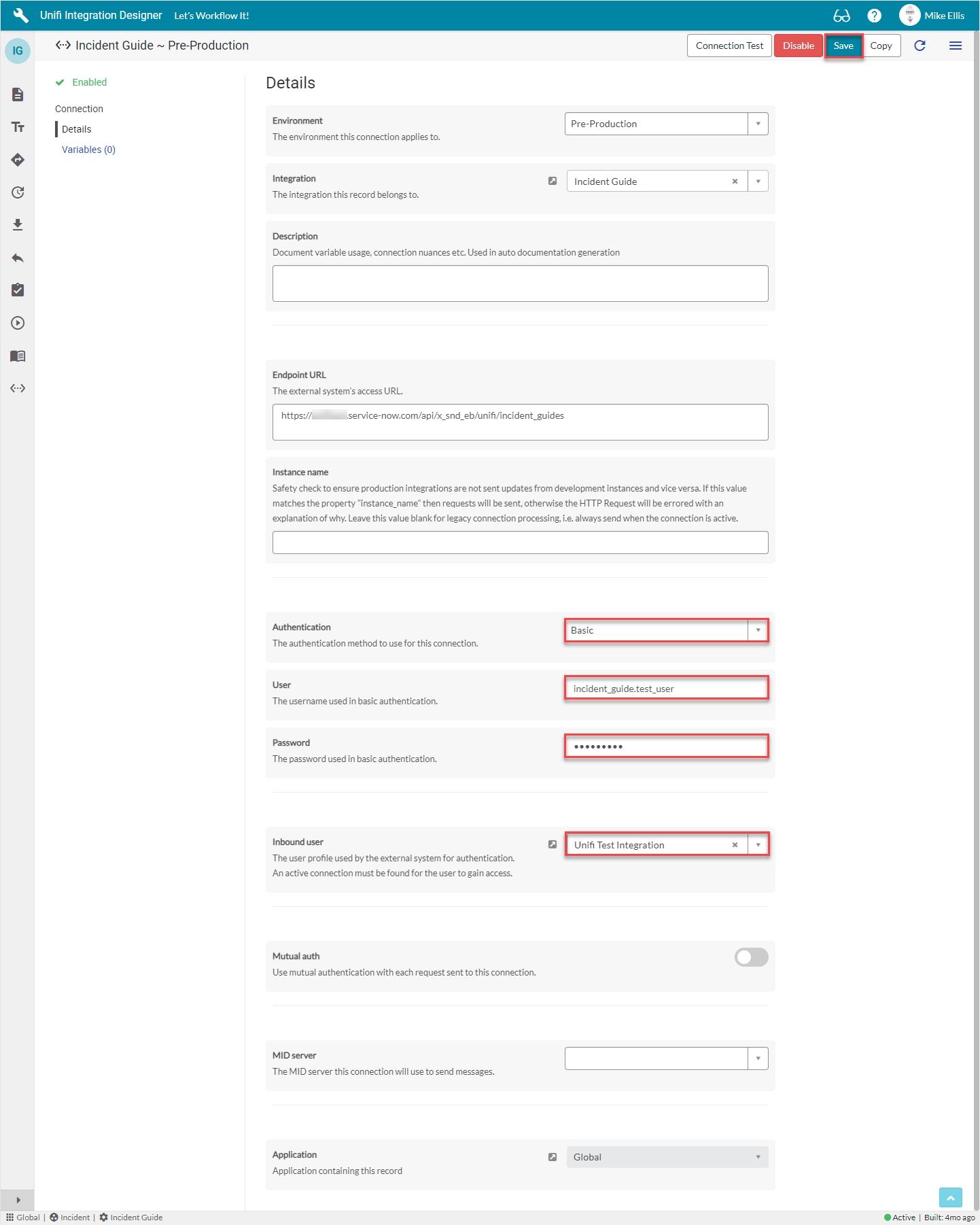
Although we will be providing an OAuth Token for the external instance to consume when connecting to this instance, we will use Basic authentication to connect outbound with the Consumer Instance.
The fields to be configured for the Details form are as follows:
Authentication
The authentication method to use for this connection.
'Basic'
User
The username used in basic authentication.
<external.system.user>
Password
The password used in basic authentication.
<External system user password>
Inbound user
The user profile used by the external system for authentication. An active connection must be found for the user to gain access.
lookup: <Your Inbound User>
Your Details form should look like this:
Save the Connection.
At this point you can perform a basic Connection test. For instructions, see here.
Next, configure the Identity Consumer Instance.
Setup a scheduled job to ensure refresh tokens do not expire.
We recommend customers using outbound OAuth use this scheduled job script to ensure outbound OAuth connections remain alive, as explained in this KB Article from ServiceNow.
Without this job, the refresh token will eventually expire which means ServiceNow will no longer be able to retrieve an access token. This in turn will cause outbound requests to fail.
If your OAuth service is including refresh tokens with each access token request, this job may not be required.
This script has been reformatted from the KB Article for ease of use.
Follow this guide to learn how to setup an OAuth Connection in Unifi.
This guide gives step-by-step instructions on how to setup an Oauth Connection for your Unifi Integration (ServiceNow to ServiceNow).
This document will guide you through the process of configuring an OAuth Connection for your Unifi Integration (ServiceNow to ServiceNow). This will involve making configuration changes in both the identity provider and identity consumer instances. As such, this guide will examine the changes for each instance separately on the subsequent pages.
In this guide, you will configure an additional OAuth Connection to another ServiceNow instance as part of the Incident Guide Integration (created when following the Bidirectional Asynchronous Incident Guide). The external instance will act as the Identity Provider whilst the original instance will act as the Identity Consumer.
It is assumed that the Integration has been configured, packaged and moved to the external instance (see here for details). Therefore, the Process, Web Service & Integration are already in place (if not, please ensure that at least those elements are in place before continuing).
These are the configuration changes to be made in the identity consumer instance when setting up an OAuth Connection.
In native ServiceNow, navigate to System OAuth > Application Registry and click New.
On the interceptor page, click Connect to a third party OAuth Provider.
The fields to be configured for the Application Registry record are as follows:
Name
Name of the OAuth app
<Your Unique Name>
Client ID
The client id of the OAuth app
The Client ID from the Identity Provider Instance
Client Secret
The client secret of the OAuth app
The Client Secret from the Identity Provider Instance
Default Grant type
The Default Grant Type used to establish the OAuth token
'Resource Owner Password Credentials'
Refresh Token Lifespan*
The number of seconds a refresh token issued will be good for
8,640,000 (default value - automatically populated)
Token URL
OAuth token endpoint to retrieve access and refresh tokens
'https://<your-provider-instance>.service-now.com/oauth_token.do'
Comments
Comments about the OAuth app
<Your description of the purpose of the OAuth entity>
*This value is to be left as-is.
Token URL: Replace the <your-provider-instance> element of the URL with that of the Identity Provider Instance.
Your Application Registries New Record should look like this:
Right-click and Save to remain on the record.
Validate that the OAuth Entity Profiles related list has been populated with the following values:
Name: <Your Unique Name> default_profile
Is default: true
Grant type: Resource Owner Password Credentials
This is the profile which will be selected when configuring the Connection.
In Unifi Integration Designer, navigate to Connections and click New.
We are going to configure a Connection for the Pre-Production environment because we have already configured connections for both the Development and Test environments. Choose whichever environment is appropriate for your requirements.
The fields to be configured for the New Connection modal are as follows:
Environment
The environment this connection applies to.
'Pre-Production'
Endpoint URL
The external system's access URL.
<External system Endpoint URL>
Active
Use this connection for the integration when true.
<true>
The format of the Endpoint URL is as follows:
https://<your_provider_instance>.service-now.com/<your_provider_process_api>
The entire Endpoint URL can be easily obtained from the automatically created Message Resource on the Unifi Scripted REST API (displayed in the widget at the top of the Connections page in the other instance).
Your New Connection modal should look like this:
Submit and view to further configure the Connection.
The fields to be configured for the Details form are as follows:
Authentication
The authentication method to use for this connection.
'OAuth 2.0'
OAuth Profile
The OAuth Entity Profile to authenticate with.
'<Your Unique Name> default_profile' (as created/validated above)
Inbound user
The user profile used by the external system for authentication. An active connection must be found for the user to gain access.
lookup: <Your Inbound User>
Your Details form should look like this:
Save the Connection.
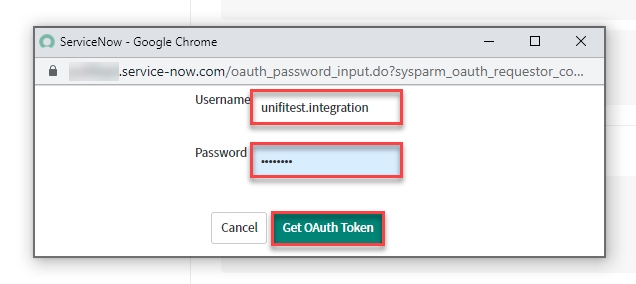
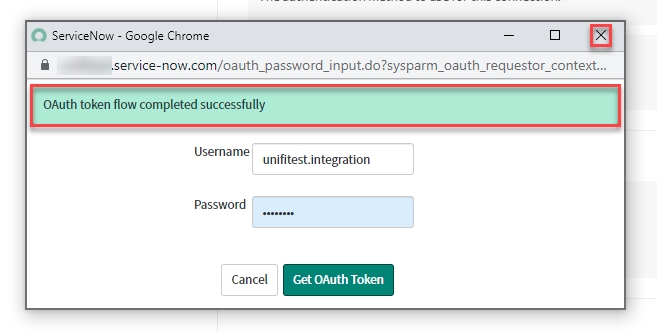
Once you have saved the Connection, the 'Get OAuth Token' button is available.
Click Get OAuth Token.
On the modal that pops up, enter the Username & Password (for the Inbound user of the Identity Provider Instance).
Click Get OAuth Token.
The 'OAuth token flow completed successfully' info message is displayed. Close the modal.
Congratulations. You have successfully configured both halves of the OAuth Connection.
To future proof your OAuth connection, please consider setting up the OAuth Refresh Token Job.